Fraud Prevention Techniques
There are many industries that are targeted by fraud each year costing businesses billions of dollars. Fraud is not something that can be eliminated entirely, however with better monitoring and verification methods the amount and impact of fraud can be reduced. A major goal with any fraud prevention technique is to make the cost of committing fraud more expensive then what is actually gained from committing fraud itself.
One of the biggest challenges with fraud detection technique in SAAS applications (specially B2C) is the more strict the fraud detection methods get, the more friction it causes in sales and the onboarding process. This friction can lead to loss of business.
The image shows some of the different fraud prevention techniques I’ve worked with and their effectiveness compared with the friction they add.
IP Analysis
In a perfect world every user would have a static dedicated IP and they would only be able to connect to the internet using that address. Unfortunately this is not the case. There are various methods to mask your true IP address. While you might consider blocking users that try to connect using anonymized IP addresses, however this poses it’s own set of challenges:
- Many businesses use VPNs when connecting to the internet. Blocking VPNs and proxies might block access to these users
- Detecting whether a user is hiding their IP is not always straight forward.
The image below shows some of the different methods for masking your IP address and how much they cost in comparison with how difficult they are to detect:
Tor Networks
TOR networks are one of the easiest to detect. They have a large footprint and using any IP analysis tool you can accurately detect if the connection is coming from a TOR network. If fraud is a concern blocking these type of connections is a must.
Data Center VPNs and Proxies
These are your typical VPN providers (i.e NordVPN). They could also be cloud hosting services that fraudulent users have setup VPN servers on. Similar to TOR networks detecting these connections are quite simple. As an example 45.9.251.2 is an IP address of a cloud hosting company called m247 Ltd. Using IPQualityScore (an IP analysis service) you can see it clearly detects this as a datacenter IP address:
While blocking all VPN and proxy connections may not be a good idea (as mentioned above due to some businesses running behind such connections), however this could be a good indicator to ask these users for additional verification.
Residential Proxies
This is where things get really complicated. Residential proxies are essentially proxy servers setup on devices connected to residential ISPs. These are normally devices that belong to regular users who fall into one of the following categories:
- Their device has been targeted by malware and is now serving as a proxy to fraudulent users
- Willingly installed a software on their device to create a proxy server for other users (in exchange for a payment of some sort)
It’s not just a matter of being able to detect these type of connections but also what to do when such connections are detected. Many of these connections are legitimate users who may not even know their device is operating as a proxy.
It gets even more complicated when you look at services provided by websites such as https://oxylabs.io/pricing/residential-proxy-pool. Oxylabs and similar websites provide whitelisted dedicated residential IP addresses. These IP addresses are nearly impossible to detect.
IP Analysis can only take you so far in preventing fraud. If you’re in an industry where false negatives can greatly harm your business then you may want to consider IP analysis to filter as many potential fraudulent users as possible. On the other hand in industries where losing business due to false positives is a higher concern, IP analysis is not the best solution.
Email Verification + Fraud Risk Score
Email verification on it’s own is not very effective. There are many sites such as https://temp-mail.org/en/ that generate throw away emails every day. Thinking about creating a list of domains to block? That won’t be very easy. People have already tried creating such lists and new domains appear every day:
- https://raw.githubusercontent.com/wesbos/burner-email-providers/master/emails.txt
- https://gist.github.com/michenriksen/8710649
What I’ve found to be very helpful though are external services that provide fraud scores for email addresses:
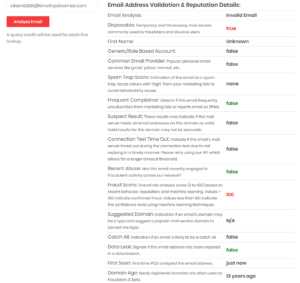
The way these services work is you would provide them with an email address and they will provide different sets of information about the email address. This information can be used to determine whether the email is legitimate or not. For example the screenshot below is from IPQualityScore:
By integrating email verification with email fraud score services, you can ultimately block out all throw away email providers. There is however other risks involved with using email verification alone. There are many legitimate email accounts that may have been compromised. There are also service that offer verified email accounts from major provides such as gmail and yahoo (https://woorke.com/buy/gmail-accounts). So once again if you choose to use email verification you should keep in mind that it will not keep all fraud out.
Phone Verification + Fraud Risk Score
Phone verification is when a code is sent to the users phone (either through a text messages or phone call) and they must verify the code. Same as email verification this is not a very useful method on it’s own. There are 100s of sites like these https://smsreceivefree.com/ that provide free disposable sms numbers for verification. They also frequently rotate their numbers so there will always be new numbers to use. There are also services that offer premium numbers (such as https://quackr.io/) which are not publicly available, making them even harder to detect.
What does make phone verification useful is combining it with a fraud score service. There are several different platforms that offer this service:
This is what a phone score lookup from Telesign looks like:
{
"numbering": {
"original": {
"complete_phone_number": "19518773108",
"country_code": "1",
"phone_number": "9518773108"
},
...
},
"phone_type": {
"code": "5",
"description": "VOIP"
},
...
"risk": {
"level": "high",
"recommendation": "block",
"score": 959
}
}
The api returns a score from 0 to 1000. The higher the score the higher risk. As you can see at the end it returned a score of 959 (meaning very high risk). The number was actually a free disposable sms number:
Payment Verification
I personally did not have really good experience with this type of verification. Not only did it cause a lot of friction, I also found it to be very ineffective. The way I incorporated payment verification can be seen below:
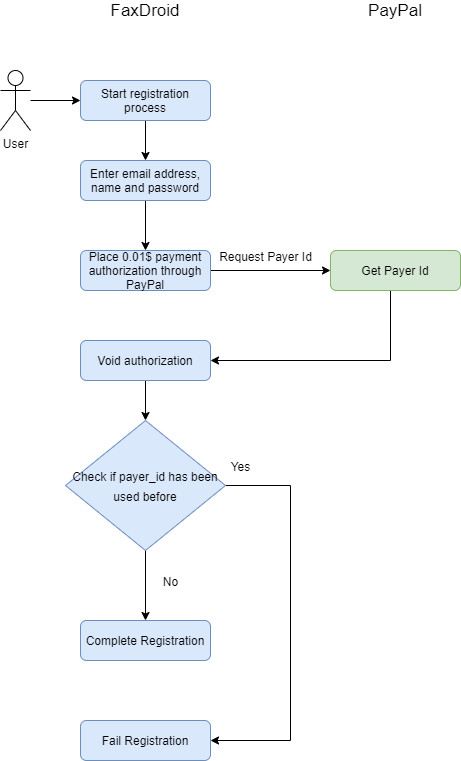
When users wanted to open an account I would place a $0.01 payment authorization on their credit card (https://developer.paypal.com/docs/api/payments/v2/#authorizations). This was done through PayPal. PayPal would return a Payer Id which I would compare with previous accounts that had been opened. In theory if the users ends up using the same credit card the same Payer Id will be returned from PayPal.
The flaw in the design quickly showed itself after learning about services such as https://privacy.com/ which allow users to generate one time credit cards. This made the verification quite pointless as users were creating one time credit cards and constantly creating new Payer Ids.
Payment verification might have worked if the payment processor provides additional information about the credit card, such as issuing back. That additional information can be used to block certain cards types. Unfortunately in the case of PayPal the only information that is returned is the Payer Id which was not very helpful.
Sales Agent Call + Company Information Inquiry
I never used this approach as the overhead and friction was too high, but I would imagine this to be one of the best ways to prevent fraud. Basically when someone wants to register an account you would have a sales agent call or send them an email. During this contact the sales agent would gather information about the client. Information such as:
- The company name
- The company website
- Any social media sites associated with the business
- Where the company is located
- …
While this can be a very effective method, it has high friction. Users will start to look at competitor’s services while they are waiting for a callback. The method also does not work well for non business customers or users that are just starting out a new business as they probably may not have most of the information above. By looking up information about the company (any news articles, online reviews, social media followers, …) you will get a good idea if this is a throw away account or a legitimate user. Combined with email verification you can confirm if the website actually belongs to the user or not.
Conclusion
In this article I’ve explained some of the different methods that can be used against fraud prevention based on my personal experience. While there is no way to prevent all fraud but most fraud prevention methods will help at reducing it. Two main deciding factors for choosing the best fraud prevention solution are:
- How much will fraudulent users gain from abusing the system
- How much will it cost them to commit fraud
Essentially at the end of the day you need to find a way to make the cost of committing fraud exceed the gains.